NewYou can listen to Fox News articles now!
As you Scroll through X (formerly Twitter)You may encounter Elmo, a cute red monster cherished by kids and parents, sharing cheerful, family-friendly content. However, recently, the official Elmo account has suddenly posted hate speech, racist slander and political attacks. This shocking violation turns beloved feed into a source of chaos and pain.
The team behind Elmo Sesame Workshop took action quickly to remove offensive posts, but for millions of fans, it has already caused losses. This is much more than a typical hacker. It represents a digital loss for one of the world’s most trusted child idols. This incident emphasizes that in today’s online landscape, there is no account, and even the safest statement is Immune to attackers.
Sign up for my free online report
Get my best technical tips, emergency security alerts and exclusive deals delivered directly to your inbox. Plus, you’ll be visiting my Ultimate Scam Survival Guide now – Free when joining me cyberguy.com/newsletter
Invaded Elmo X account shocks users with “Kill All Jews” and “Post File” posts

Elmo’s official verification X account (@elmo on x)
Social media network security risks are trustworthy brands
Hackers are eager to reach and pay attention, and few have the goal to offer more than just a beloved global brand. When an attacker captures hundreds of thousands of followers’ control over the account, they immediately access their information, whether it’s false information, hate speech or targeted harassment. The Elmo incident is not about stealing data or redeeming an account; it is about causing chaos, sowing a split and destroying trust.
Elmo’s online voice has been synonymous with joy and support for many years. Followers have been violated as they question how such ugly characters can behave like such ugly characters. The reputation of the brand that has been built for decades has been compromised within minutes.
As Sesame Workshop put it, “End gatherings briefly invaded Elmo’s X account despite security measures. We strongly condemn the abominable anti-Semitism and racist content, and the accounts have been secured since then. These positions in no way reflect the value of Sesame Workshop or Sesame Street, and any of the organization.”
The incident underscores the importance of strong cybersecurity measures, especially when trusted brands act as platforms for millions of globally.
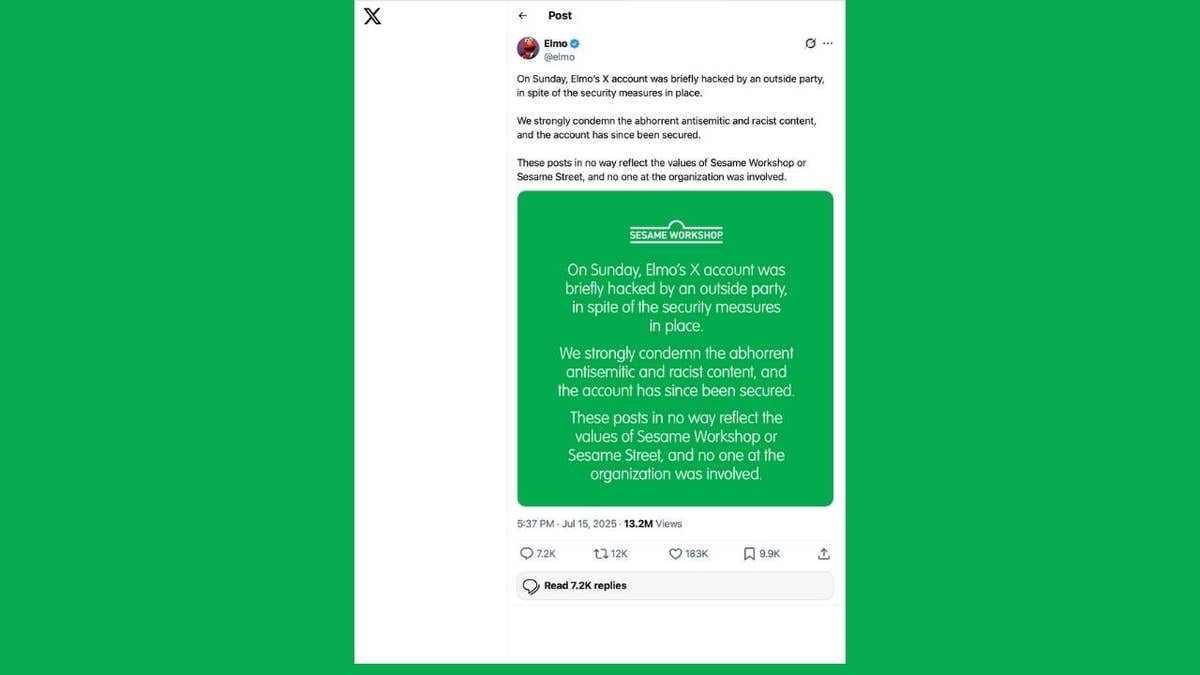
Sesame Seminar Statement after Elmo X Hack (Elmo’s X account)
Why social media accounts get hacked (even with “strong” security)
To better understand what’s going on, we turned to Daniel Tobok, CEO of Cypfer, a world-leading cybersecurity and incident response company. Daniel spent more than 30 years guiding the organization to carry out major online activities.
“Although passwords have strong passwords or MFA barriers, many credentials were harvested on the dark web among different groups of threat participants. Maybe someone lost the password, or the administrator saved it on a laptop, which was part of another violation. Once those passwords were collected, they were collected or sold.”
Although brute force attacks are still happening, most criminals don’t waste time hammering complex passwords. Instead, they take advantage of the simpler route: snatch passwords from old vulnerabilities, target users directly or hijack password vaults, especially passwords managed by social media administrators.
“Brute force attacks can cause a lot of noise and can trigger alarms. This is no longer the most popular strategy because it is so noisy.”
Warning signs Your social media account may be hacked
Unfortunately, you may not warn that your account is targeted.
“You are not actually notified of your public-oriented software. Sometimes, you may receive an email saying ‘We noticed unusual activity. Is this you?’ This is usually via the MFA channel, but most executives don’t do it on their social media accounts.
Hackers can even set rules to rearrange security notifications from your inbox, leaving you completely unaware of any problems until it’s too late.

A woman scrolling on social media on smartphone (Kurt “Cyberguy” Knutsson)
Common social media security errors to avoid
Hackers expect you to be complacent. Daniel summons traps to avoid:
- Not verified your account
- Reused or unable to rotate passwords
- Skip MFA (Multi-factor authentication)
- Assume that “this won’t happen to us”
Daniel added most shockingly: “Most people’s information has been compromised at some point. There are currently more than 4.8 billion passwords scattered on the dark web. Finally, never reuse the same password on multiple platforms. I know it’s boring, but the correct hygiene is like this.”
What is artificial intelligence (AI)?

A man scrolling on social media on mobile phone (Kurt “Cyberguy” Knutsson)
What to do if your social media is compromised
Action quickly. Here is Daniel’s step-by-step plan:
If you are still accessible, change your password now. Most threat participants will immediately change their passwords and emails linked to their account so that they have full control. If you are locked, you need to contact the platform and provide proof that it is your account. Ask them to turn it off or help you recover quickly.
Key Steps to Protect Your Social Media Account
Protecting your social media account is more important than ever. Follow these steps to strengthen your cybersecurity and limit your hacker bureau:
1. Use a powerful unique password
Create a password of at least nine characters, mixing uppercase, lowercase, numbers and symbols. Never reuse passwords on the platform and update them regularly for maximum protection. Consider using Password Managerit can safely store and generate complex passwords, reducing the risk of password reuse. Also, use a password manager instead of sending a password through an unencrypted message. Password Manager allows you to share credentials when absolutely necessary and helps prevent security leaks.
Check out the best expert review password managers in 2025 cyberguy.com/passwords
2. Enable Multi-Factor Authentication (MFA)
always Activate MFA Add an additional layer of login protection. This makes it difficult for unauthorized users to gain access even if your password is compromised.
3. Set up suspicious login activity alerts
Take advantage of account alerts and limit unsuccessful login attempts to quickly detect intruders. Review these alerts regularly so you can respond immediately if there are some situations off.
4. Verify your account through the platform
Apply for official account verification where possible to add additional safeguards and make recovery easier. Verification can also prevent imitation and build trust with your audience.
5. Update account recovery information
Check and keep your recovery email and phone number current to regain access if needed. When you need to restore your account the most, outdated information may lock you.
Click here to visit Fox Business
6. Review third-party application access
Delete applications or services that you no longer use; these can become weaknesses if compromised. Regularly review connected applications to ensure that your data is not revealed through unused integrations.
7. Back up your content and followers
In the event of an account being lost or locked, use platform features or trusted tools to back up important data. If you lose access or accidentally delete data, this simple step might be a lifeguard.
8. Using powerful antiviral software
Install powerful antivirus software on all devices used to access social media. Regular updates and real-time scans protect you from malware and phishing that could harm your account. The best way to protect yourself from installing malware (malicious links that may access private information) is to install antivirus software on all devices. This protection can also remind you about phishing email and ransomware scams, ensuring your personal information and digital assets are secure.
Choose from the Best Antivirus Protection Awards for Your Windows, Mac, Android and iOS devices cyberguy.com/lockupyourtech
9. Consider deleting data
Reduce digital footprint and minimize risk by using services that remove your personal information from data brokers and people’s search sites, especially after vulnerabilities. These services make it harder for criminals to collect sensitive data used in social engineering attacks. While there is no service that guarantees complete deletion of data from the Internet, a data deletion service is indeed a wise choice. They are not cheap, nor are your privacy. These services provide you with all your work by actively monitoring and systematically deleting your personal information from hundreds of websites. This is where I feel at ease and proves to be the most effective way to delete your personal data from the internet. By limiting the available information, you can reduce the risk of cross-references of data from fraudsters in violations and find information on the dark web, making it harder for them to target you.
Check out my preferred data deletion service and scan it for free to see if your personal information is already accessible on the internet cyberguy.com/delete
Do a free scan to find out if your personal information is already on the Internet: cyberguy.com/freescan
10. Perform general security settings audits
Check out your social media privacy and security settings regularly to make sure they meet your current needs. The platform will usually add new settings and features and stay up to date to provide you with the best protection.
11. Use public Wi-Fi with caution
Avoid logging in to your account Public Wi-Fi Or always use a VPN. Public networks make it easier for hackers to intercept your information.
For the best VPN software, see my expert review of the best VPNs to browse the web privately on Windows, Mac, Mac, Android and iOS devices cyberguy.com/vpn
12. Delete the former employee or administrator immediately
Regularly review account access and revoke those who no longer need it. This ensures that only trusted individuals can post or make changes on your behalf.
Click here to get the Fox News app
Kurt’s key points
Elmo Hack is more than just a cheerful digital character. It reminds us that no matter how trusted, there is no brand that is immune to today’s cyber threats. In an environment where trust is built through tweets, it has never been so urgent to protect our digital presence. Social media security is everyone’s responsibility. Take action before becoming the next viral course that doesn’t do anything.
Do you think social media companies are doing enough to protect users and brands from evolving cybersecurity threats? Let’s write to us cyberguy.com/contact
Sign up for my free online report
Get my best technical tips, emergency security alerts and exclusive deals delivered directly to your inbox. Plus, you’ll be visiting my Ultimate Scam Survival Guide now – When Joining Me cyberguy.com/newsletter
Copyright 2025 CyberGuy.com. all rights reserved.






